I'm going to preface this particular post by saying that I am by no means a subject matter expert on this or most other security topics, cyber or otherwise: I'm merely a cybersecurity-adjacent and interested IT technician and person who enjoys being extra curious. that is where my qualifications begin and end.
With that said: let me make my case. I recently moved to a new city which unbelievably, is (1 in the USA and (2 has functional and fairly reliable public transit. Insane, I know, but I promise I'm not being hyperbolic. As a result of this change in life plans, I've been doing a whole lot more walking, as I've more extensively used public transit to get around.
At the same time, our new dear leader, Donald Trump was elected - and in my life, what came with that occurrence was a stark, deafening feeling of civil unrest and as a result, there were huge protests filling the streets of my new city for several days.
These events, though seemingly unrelated, had an impact on how I saw the city and my world in general, as I traversed my surroundings, made friends, and looked for work. I experienced a shift in perspective, in near-realtime. I watched my view of the infrastructure that I relied on, change from "this is nice!" to a much more grim "how would I attack these systems if I were forced or inclined to do so?" sort of vibe. This perspective brought more dreadful answers than I would have liked: bad actors could seriously fuck this whole thing up with a few well-timed moves, I soon discovered.
For safety, I've obfuscated the locations of these installations to prevent silliness and to protect my identity. However, these are real installations in a real city in the United States.
Sadly, I don't have a lot of experience in high-voltage electronics or anything of the sort, but I do know that high-voltage infrastructure is both important and very easy to attack: especially when the attack is just...turning off a switch. This switch was accessible from a sidewalk along the side of a very large pharmaceutical manufacturing facility and office - thus the large breakers and cooling systems.
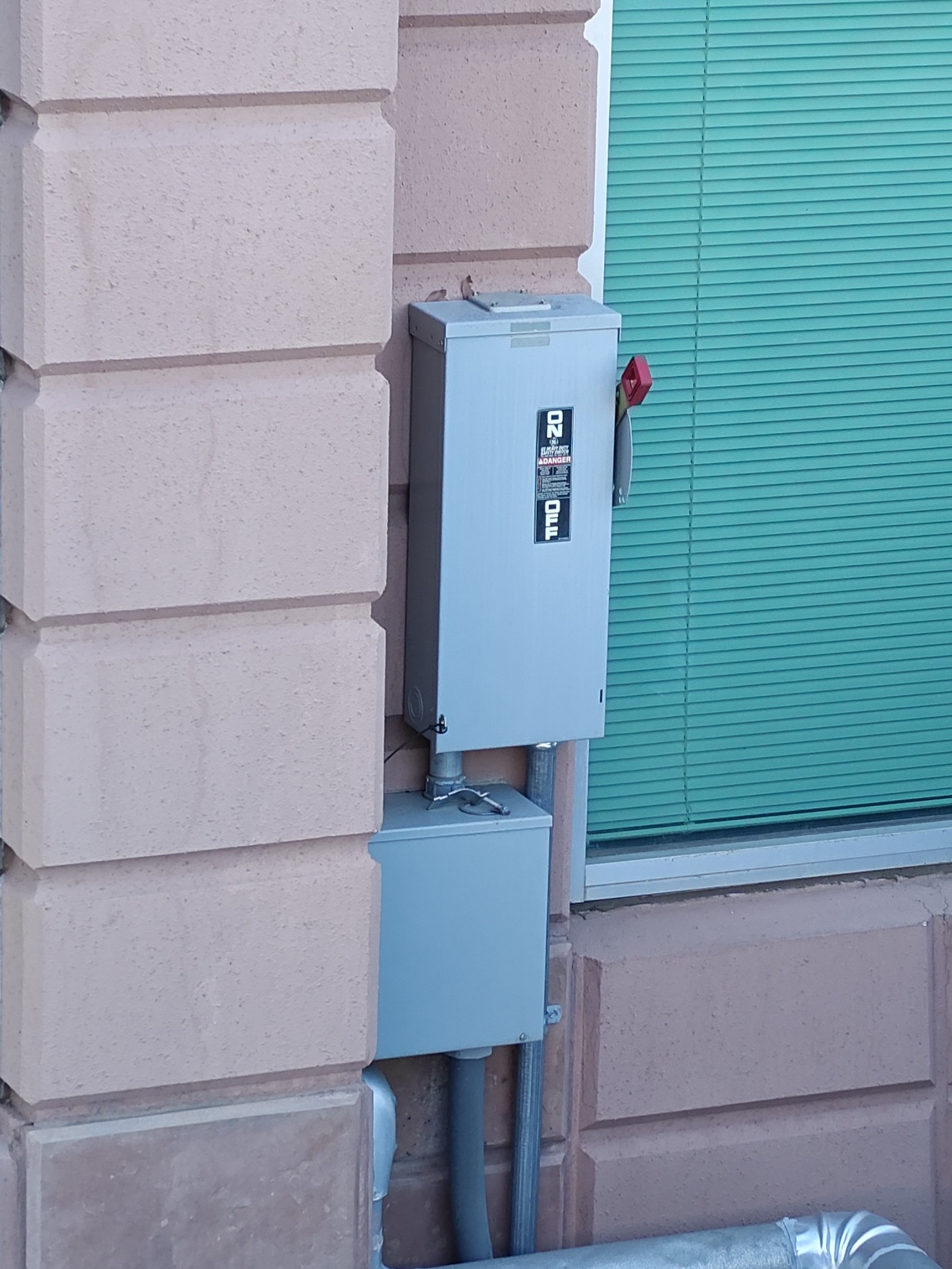
or...turning off 3 to 4 very large breakers which power a large apartment complex, and are (not entirely) protected by "wtf-is-this" brand-name locks that are severely rusted, and not at all pickable.

Yes, power is important, but oftentimes, telecoms are similarly important, even in an outage - and in some cases, more so. Cell sites need to stay up for emergency calling, internet backbones carrying first-responder radio and MDT traffic can't go down, and emergency medical service providers like hospitals must be able to talk with inbound ambulances and between their teams using IP-based pagers, even if the power is out. So, it would be unfortunate and potentially life-threatening if that critically important stuff were to be attacked, but thankfully it's well secured. right?...oh. oh no.

This unassuming little box contains lots of cool stuff, and it would be a shame if a careless and/or underpaid technician left it unsecured and open.

These are just the examples I've found while walking through my city on foot and just looking at my surroundings: I wasn't even trying to find these, and this doesn't include the myriad keyed-alike vehicles, traffic light controller cabinets and hardware, building locks, and the like, that are vulnerable to similar, if not identical attacks. A motivated attacker might log the locations of these unsecured access points and systems and coordinate a strike on them in the future, or worse, wiretap them for maximum effect - similar to the US' bombing attacks on switching centers during Operation Desert Storm in the Middle East.
I could go on - but at this point, I think you get the gist: if a team of even tangentially knowledgeable attackers were to coordinate an assault on these wildly vulnerable and exposed weak points, it would hold the potential to be highly costly - not just hard on the pocketbook, but on the obituaries.
It would be cheap for them too: a few masks, pocket knives, radios, maybe a lockpick kit or two, and a reciprocating saw would run them less than $1000, and would allow a small team to cripple a city in minutes.
No need for SALT TYPHOON, for stockpiles of 0days in industrial control device firmware, or anything of the sort - after all, why break into the network by force when you're given free ports on the sidewalk?
So, what do we do? I think a good place to start is to standardize, vet, and put up for professional comment, security standards for public infrastructure and related equipment. Make it public, and allow physical security professionals to hone in on the issues I've missed. Long story short, we need to stop ignoring this glaring threat to our literal safety, and start asking what we can do - that's a good start.
tilde.town/~echol0cation and all its subdirectories and files by @echo.bladehook.org are licensed under CC BY-NC 4.0