Project Cyan
05 April, 2018
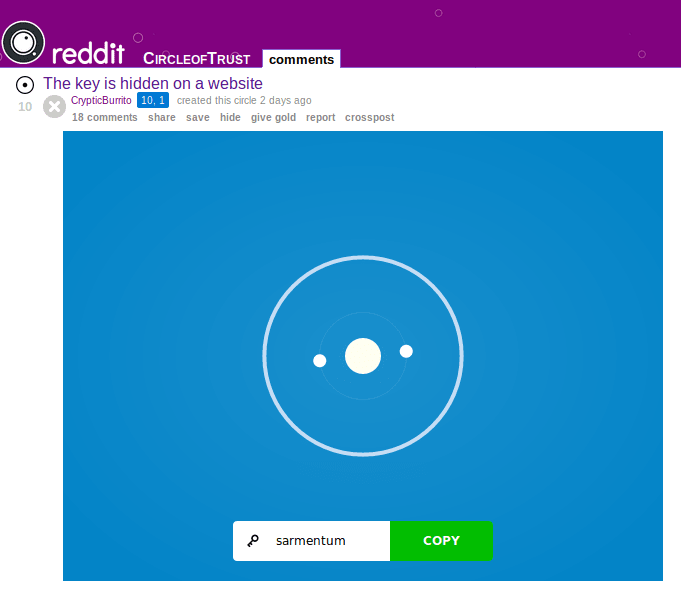
On April 2nd 2018, Reddit launched its April Fools social experiment for the year: Circle of Trust. The game allows each account to create their own circle with a password. On gaining the password to another user’s circle, you can choose to join or betray. Betraying a circle destroys it, disabling any new members from joining. A score is kept and displayed for each user with the size of their circle and the number of unbetrayed circles they are in. If the user has ever betrayed a circle, their score is displayed in red.
Inevitably some users were going to place their password behind a CTF-style game, and this happened in the form of Project Cyan by user /u/CrypticBurrito. The website declares itself as a member of the “Zaffe Research Consortium”, a group of friends also responsible for a circle that involved calling a freephone ‘helpline’ number, which was very fun.
The frontpage of the website has a suspiciously hidden link which requires an HTTP basic auth username and password, as well as two items that look suspiciously like hashes. Inspecting the source reveals a third, longer one. Using CyberChef and the ‘Analyse Hash’ function, we can see that the smaller hashes are likely MD5, and longer seems to be SHA256. Using a hash cracking website, we get the following:
21232f297a57a5a743894a0e4a801fc3MD5 : admin52532fca717f146b16e91fc3a96f843fMD5 : projcya8271bb66dfb7999c3b533c5cdef9f4a477876dccd0fdd27b9f762f7951ac595SHA256 : tetrahedral
The first two look like the username and password, and sure enough they are.
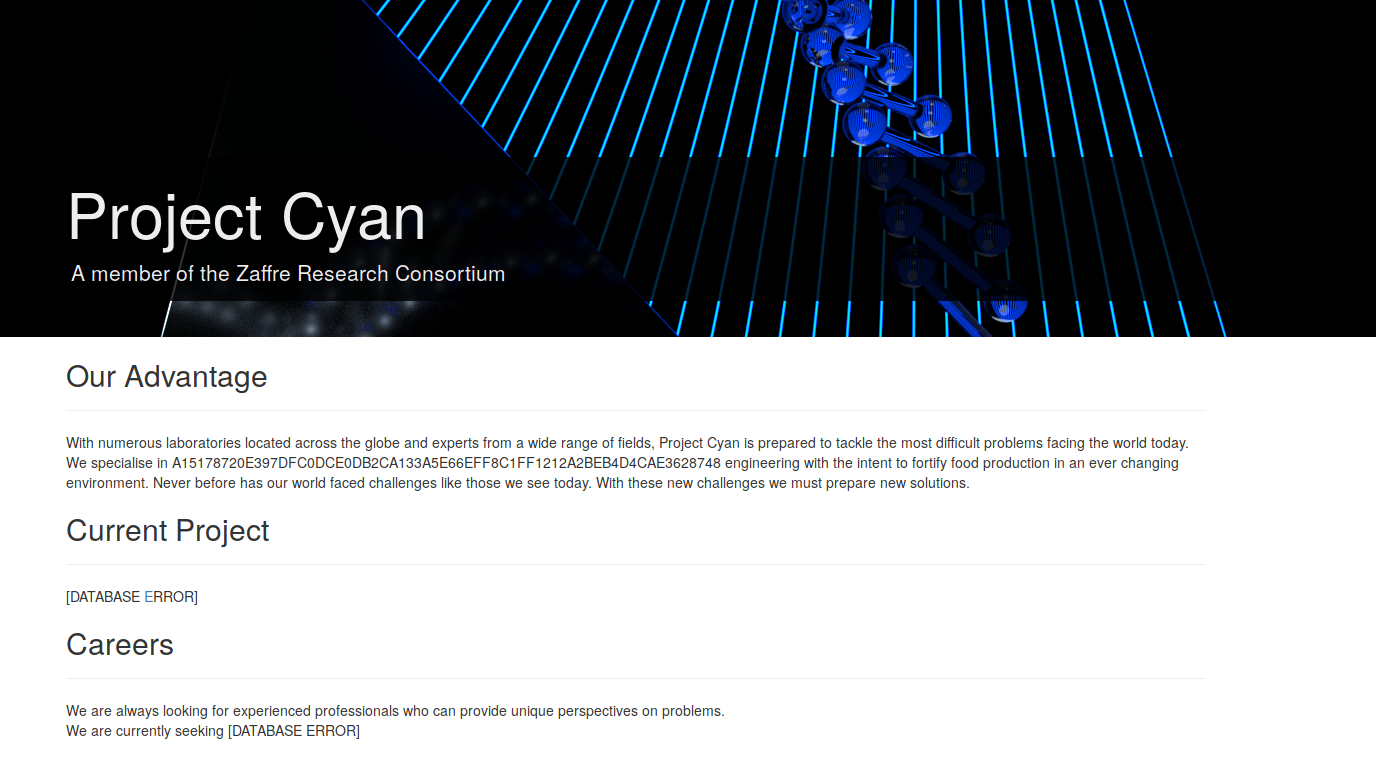
This brings us to a simple text page with a few links. To begin with, we have
two more hashes, each containing a sly link to a seperate login page. The first
goes to north/north.html, and the second goes to windle/windle.html. Next we
have a list of emails, and another password-protected link named
‘Office Directory’ to the page direc/list.html.
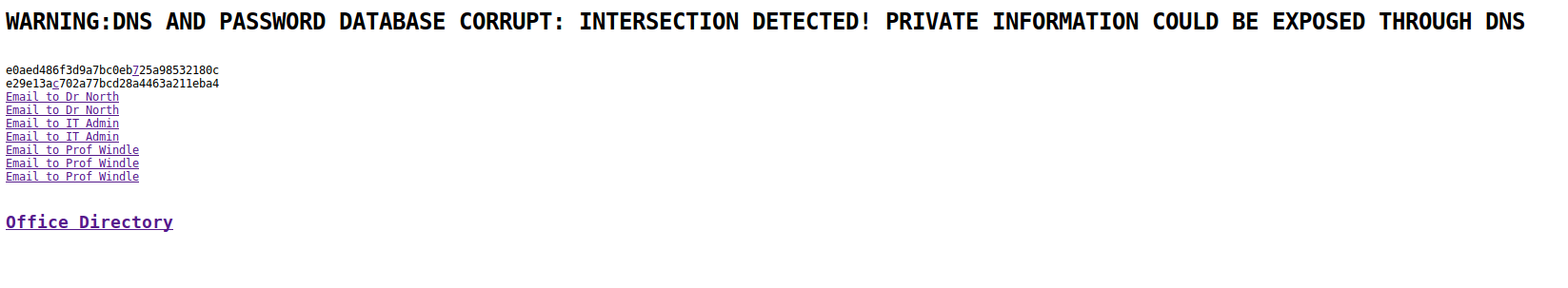
Let’s begin to unpack this. The hashes crack to:
e0aed486f3d9a7bc0eb725a98532180cMD5 : automatone29e13ac702a77bcd28a4463a211eba4MD5 : helicopter
The emails are as follows:
- Email to Dr North
You were always talking about this being your favourite [img]- Email to Dr North
--THIS IS AN AUTOMATED MESSAGE--
We have detected multiple failed attempts to access your account.
When did you last reset your password?- Email to IT Admin
--THIS IS AN AUTOMATED MESSAGE--
IT Admin please run recovery on DNS system- Email to IT Admin
--THIS IS AN AUTOMATED MESSAGE--
Intersections detected in the following databases:
- DNS TXT Records
- User Passwords- Email to Prof Windle
--THIS IS AN AUTOMATED MESSAGE--
Prof Windle, your password has been automatically reset.
Your new password has been sent to your phone.- Email to Prof Windle
Don't worry, I had a plan for this.
Remember that picture you made me?
- North- Email to Prof Windle
I hid the password in that picture you made me. It'll be hard to find for most
people, but obvious to you since you know where to look. I convinced the IT
admin to add a hex editor to all our workstations. Also, the IT admin is mad at
you for trying to replace one of your verification words with a caesar cipher.
- NorthThat last email gives us a lot to go off. If we go to the image from the first and look at it in hex editor, we indeed see at that the very bottom contains a password:
The password is dancepartycentral the username is office
The username of office seems to hint that these are the credentials for the
‘Office Directory’ at the bottom, and sure enough they are. Access to this page
gives us the following:
Prof Windle: (604) 359-6048This is a British Columbia (Canada) phone number. This appears to be a dead end for now, since I can’t call this number as I am not in Canada. Continuing, we see that the main page as well as multiple emails mention the DNS records, specifically the TXT records., and how they could potentially be leaking sensitive information.
$ nslookup -type=txt projectcyan.pw
Server: 192.168.0.1
Address: 192.168.0.1#53
Non-authoritative answer:
projectcyan.pw text = "windle-verif=usbjotubujpo"
projectcyan.pw text = "north-pass=v07ri6572nnu"
Authoritative answers can be found from:This gives us some useful information. The first login page is to
North’s page. We try the username north, and the password
v07ri6572nnu, and sure enough we get in. This gives another hash.
bd7fbdd6d4b03e6bce080d78fc575a22MD5 : antibody
The second goes to Windle’s. The last email describes how he used a Caeser
shift on his verification code, which appears to be what we have from the DNS
record. Playing around with it in CyberChef, we see a shift of 25 (or -1) turns
usbjotubujpo to trainstation. This is not his password, however, and goes
not grant entry. Another email mentions that his password was sent to his phone.
We have a phone number, and what seems to be a code that could grant access.
Faced with having to call the number, I privately messaged the creator of the
circle, and he generously gave me the response.
New message. Message 1. Your new password is 1, 1, 2, 1, 8, 6, 6, 4, 3, 4, 4,
9, 0, 3, 2, 7, 3. End of messages.The second login was thus username windle, password 11218664344903273. It
looks like we didn’t need the verification code after all. The page leads to a
link called ‘Your favourite song’, and links to xc_alpha.flac. Looking at the
metadata we get the following:
- TITLE=unaudited
- ARTIST=nonimaginarily
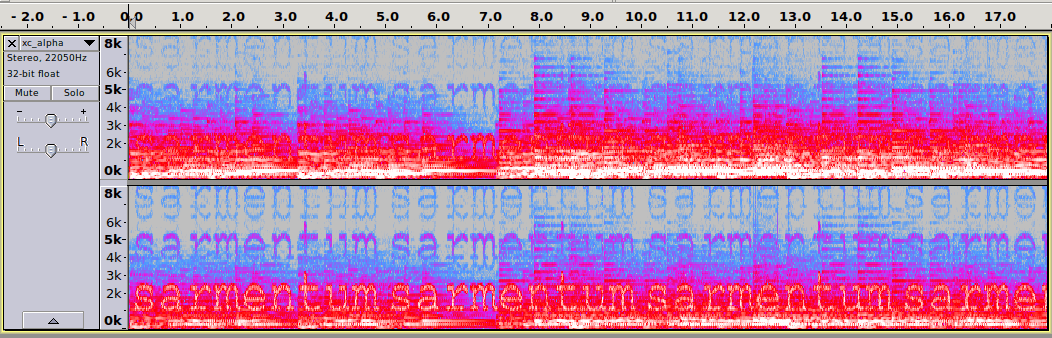
Looking at the spectrogram of this file reveals the word sarmentum. At this
point, we have exhausted all login forms and links, so it makes sense to test
the collection of words to see if one is the key. As a reminder, the remaining
words are:
- tetrahedral
- automaton
- helicopter
- antibody
- trainstation
- unaudited
- nonimaginarily
- sarmentum
The most obvious answer is that it is the one that took the most effort to get, and sure enough the key is ‘sarmentum’.