Dragon's Horde
Dragon’s Horde was the first reverse engineering challenge of SwampCTF 2018.
A single binary, adventure, is given. It is a 32-bit x86 non-stripped ELF.
On opening the file in a disssembler, we see that there are 15 functions
named foo followed by a number, and main(). The latter outputs a long story
and some ASCII art, then asks for input. It then goes through the input
performing various checks, and calling the foo functions in order if the
input matches.
Each foo function appears to be very similar. A single byte is saved to a
variable, and then appended to a global C++ string f using the plus-equals
operator. Simply put, each foo function concatenates a byte to the final flag
string.
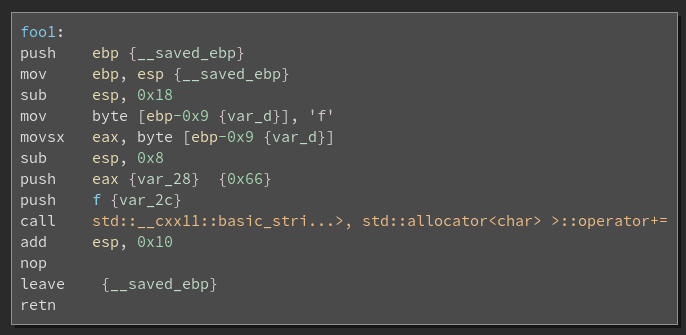
Setting this byte to display as a character (or looking up the value in an
ASCII table) confirms our suspicions, as it is ‘f’. Sure enough, the next are
‘l’, ‘a’ and ‘g’. Going through the rest of the functions in order gives us the
remaining characters to fully build the flag, flag{r3v_1t_up}.
