Protonmail isn't (and has never been) a silver bullet
So apparently the "bulletproof," privacy-protecting email provider Protonmail has been hit with a legal warrant, and was forced to submit some user data to Swiss law enforcement, which in turn was handed over to American law enforcement after harassing and death threat emails were sent from their servers.
Could it be that the once bulletproof service has broken bad and turned its back on its - apparently 50 million - users? Not at all. They are simply operating as usual, complying with the jurisdiction from which they operate.
The problem here is not that Protonmail failed, but rather that a huge number of people still think it's a one-stop shop for all their surveillance problems, a privacy silver bullet. Be it because of blind advertisement by the privacy-conscious community since its inception or the way it was showcased in Mr Robot, many still misunderstand how its encryption works, and how - essentially - you're outsourcing away your privacy by simply trusting yet another middleman.
This is not the first time that this sort of "encryption-busting" happened either. In December 2020, Tutanota, a German provider of a similar encrypted-storage email service, was also forced to backdoor the encryption of one of its users after being served a court order. Once again, the misconception of unbreakable encryption and perfect privacy by some third party provider was proved wrong.
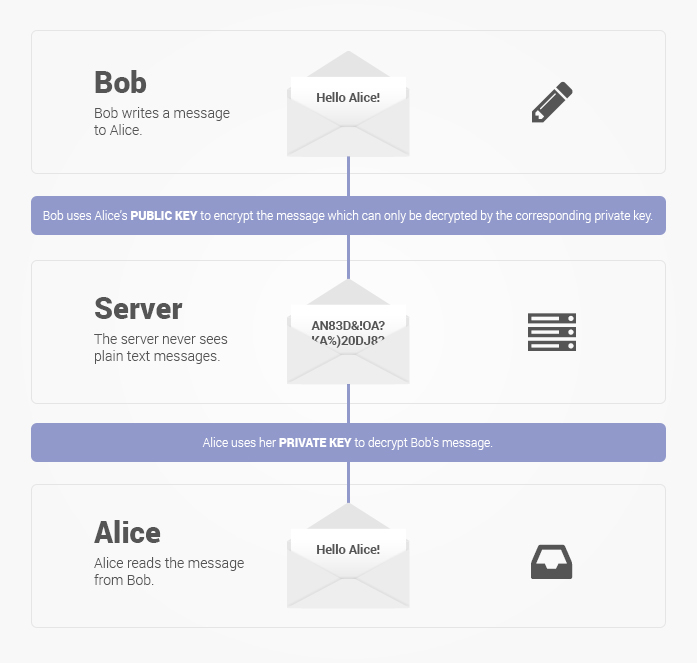
There is no way to have privacy in encryption outsourced to someone else. Want real privacy? Use GPG or some other form of end-to-end encryption, where plaintext data is never made available, unless explicitly decrypted by either endpoint of a conversation.
But don't just take my word for it: here's what Martin Steiger, a renowned Swiss lawyer specialized in Privacy and Data protection laws, has written about the ordeal (machine-translated from German):
For security authorities in Switzerland, ProtonMail is a godsend, because many users wrongly believe that their data is actually protected by the "strict Swiss data protection laws" with ProtonMail. They do not know that the applicable data protection act (DSG) in Switzerland does not guarantee effective data protection and that criminal proceedings and surveillance measures are not covered by the DSG at all
Be wary of any other online service provider that advertises itself with this model of encryption as the sales pitch. This includes not only email providers (Tutanota, Confidesk, etc), but also cloud storage providers like Kim Dotcom's MEGA. Anything that isn't encrypted or decrypted locally has the potential for a backdoor in transit to render the whole encryption moot. Actually even local encryption carries its risks, but at least the chances are much, much lower, especially if the host system is kept up to date.
What's your take on the security and privacy of services that follow the Protonmail model? Do you think it's an appropriate substitute for E2EE done locally? Let me know on Mastodon!
This post is number #25 of my #100DaysToOffload project. Follow my progress through Mastodon!
Last updated on 08/04/21